SMB Cybersecurity Report 2025:
The telco product manager's essential guide to SMB cybersecurity
This guide is designed to empower product teams in mobile/internet service providers, with the knowledge, tools, and strategies to grow your small-medium business (SMB) category. Consider it your one-stop resource, providing insights to help you better serve your existing and new, SMB customers.
What's covered in this guide?
This guide's for you if:
You’re working across product, data, or innovation within an ISP, and are looking to better understand and support your existing SMB customer base, while attracting new subscribers.
-1-2.png)
By understanding the specific cybersecurity challenges that SMBs face, you'll be able to serve them better by creating products, propositions, and value-added services that meet their needs. This enhanced understanding will help you develop more effective solutions, improve customer support, and implement robust security measures, all which help to attract and retain SMB subscribers.
-
Verizon's 2020 Data Breach Investigations Report
-
IBM Security's 2019 Cost of Data Breach Report
-
Accenture's 2019 Cybersecurity for Small and Medium-Sized Businesses report
-
The National Small Business Association's (NSBA) 2020 Cybersecurity Survey
AI-Powered Cyber Attacks: Cyber attacks that use artificial intelligence to enhance their effectiveness, often by automating processes or using machine learning to bypass security measures.
Advanced Persistent Threats (APTs): Long-term targeted attacks in which an intruder gains access to a network and remains undetected for an extended period, aiming to steal sensitive information.
Antivirus Software: Programmes designed to detect, prevent, and remove malware, including viruses, from computers and networks.
Audit: A systematic examination of an organisation's security policies, measures, and practices to ensure they are effective and comply with regulations.
BlackDice: A company providing cybersecurity solutions tailored for small and medium-sized businesses (SMBs), including AI-powered technology embedded in routers.
Cyber Attack: Any attempt to expose, alter, disable, destroy, steal, or gain unauthorised access to or make unauthorised use of an asset.
Cyber Insurance: Insurance policies designed to help organisations mitigate financial losses resulting from cyber incidents, including data breaches and business interruption.
Cyber Liability Insurance: A specific type of cyber insurance covering the costs related to data breaches, including legal fees, notification costs, and penalties.
Cyber Posture: An organisation's overall cybersecurity strength, including the effectiveness of its security measures, readiness to respond to incidents, and ability to recover from cyber attacks.
Cyber Readiness: The preparedness of an organisation to prevent, detect, and respond to, cyber threats and incidents.
Cyber Resilience: The ability of an organisation to respond to, and recover from cyber attacks while continuing to operate effectively.
Cybersecurity Audit: A thorough review of an organisation's security measures, technologies, and policies to identify strengths and weaknesses.
Data Breach: An incident in which sensitive, protected, or confidential data is accessed, used, or disclosed without authorisation.
Distributed Denial of Service (DDoS) Attack: A cyber attack in which multiple systems overwhelm a target system, such as a website or server, with traffic, causing it to become inaccessible.
Employee Training and Awareness: Programmes designed to educate employees about cybersecurity best practices and how to recognise and respond to potential threats.
Encryption: The process of converting data into a code to prevent unauthorised access, ensuring data security both at rest and in transit.
Firewall: A network security device that monitors and filters incoming and outgoing network traffic based on an organisation's previously established security policies.
Incident Response Plan (IRP): A set of instructions and procedures designed to help detect, respond to, and recover from cyber incidents.
Insider Threats: Security risks that originate from within the organisation, often involving employees or former employees who misuse their access to data.
Intrusion Detection Systems (IDS): Devices or software applications that monitor network traffic for suspicious activity and potential security breaches.
IoT Vulnerabilities: Security weaknesses in Internet of Things (IoT) devices that can be exploited by cyber attackers.
Malware: Malicious software designed to harm, exploit, or otherwise compromise a computer system.
Multi-Factor Authentication (MFA): A security system that requires more than one method of authentication to verify a user's identity for login processes.
National Cyber Security Centre (NCSC): A UK organisation providing guidance and support for cybersecurity to protect the public, businesses, and the government.
Phishing Attacks: Attempts to deceive individuals into providing sensitive information, such as usernames and passwords, by masquerading as trustworthy entities in electronic communications.
Regulatory Compliance: Adherence to laws, regulations, guidelines, and specifications relevant to an organisation's business processes.
Ransomware: Malware that encrypts a victim's data and demands a ransom payment to restore access.
Role-Based Access Control (RBAC): A method of regulating access to computer or network resources based on the roles of individual users within an organisation.
Security Audit: An official examination of an organisation's security policies and practices to ensure they are effective and compliant with standards.
SMB (Small and Medium-Sized Business): Businesses with a limited number of employees and revenue, typically having fewer resources for cybersecurity compared to larger enterprises.
Supply Chain Attacks: Cyber attacks that target less secure elements in the supply chain to compromise the larger organisation.
Vulnerability Scanning: The process of identifying and assessing vulnerabilities in computer systems, networks, and applications.

Why is this needed now?
The cybersecurity challenges faced by small and medium-sized businesses today are varied and many. These different cyber threats can disrupt operations, compromise sensitive data, damage reputations and in some cases, lead to complete closure. Unlike larger enterprises, SMBs often have limited access to the resources and expertise required to effectively combat these threats, making them prime targets for cyber criminals.
As a telecom operator, the time to act is now
Now is the critical moment for telecom operators to step up and support their SMB customers in tackling cybersecurity challenges.
As cyber threats continue to escalate, small and medium-sized businesses are increasingly vulnerable, yet often lack the resources to protect themselves effectively. By offering robust cybersecurity solutions tailored to the needs of SMBs, telecom operators can not only help safeguard their customers but also address their own pain points.
Enhancing cybersecurity offerings enables telcos to grow their SMB customer base, reduce costs to serve, improve Quality of Experience (QoE), and increase Average Revenue Per User (ARPU). This dual benefit makes investing in SMB cybersecurity a strategic move that drives both customer satisfaction and business growth.
Uncovering powerful insights from network data
Beyond just boosting cybersecurity for SMBs, telecom operators can tap into the rich potential of network data insights through advanced AI-powered tools. By analysing this data, telcos can gain valuable insights into user behaviour, identify threat patterns, and optimise network performance. These insights allow operators to anticipate and address issues before they affect customers, ensuring a smoother experience. This keeps customers loyal, happier, and gives you a competitive edge.

With this data-driven approach, there’s a real opportunity for telcos to innovate, offering tailored services that meet the specific needs of SMBs, drive new revenue streams, and ultimately help you deliver a better quality of experience to your users.
– Paul Hague, Founder and CEO, BlackDice Cyber
-
What is the market opportunity?
-
Catering to an underserved market segment
-
Unlocking new revenue streams in the SMB category
The market opportunity
Increasingly vulnerable to cyber attacks, SMBs face unique challenges that demand innovative solutions. Telecoms operators are ideally positioned to address these needs, building trust and loyalty among your SMB customers.
At present, only 10% of the cybersecurity market is served by traditional vended solutions. These consist primarily of direct-to-consumer offerings, such as signature based anti-virus, or expensive, complex solutions tailored for large enterprises.
This means there’s a huge gap between traditional vendor offerings and evolving customer needs across the entire landscape.
Cybersecurity market overview
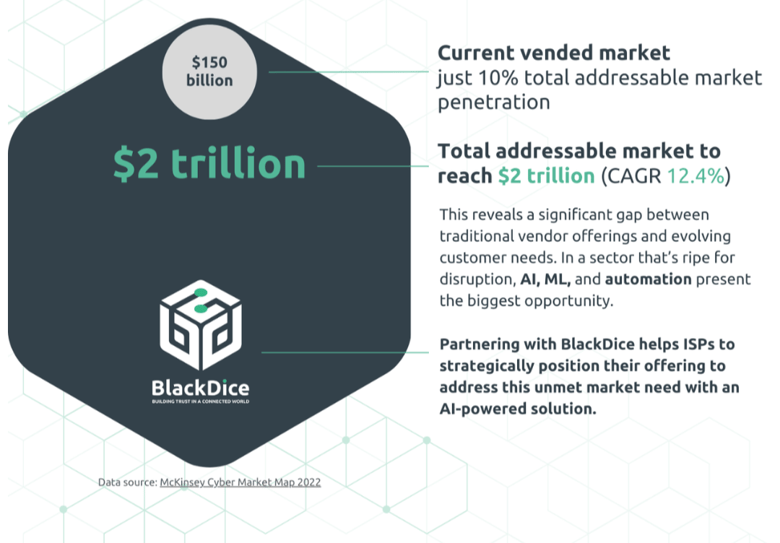
Whether you're an operator with an established SMB customer base or you're looking to grow your market share with new SMB customers; partnering with BlackDice means tapping into a $2 trillion underserved market with AI-driven cybersecurity solutions designed to evolve with your customers' needs. This provides enterprise-grade cybersecurity as a value-added service, with deep data insights and actionable analytics to secure all devices on your network.

Catering to the underserved cybersecurity needs of SMBs, our technology helps you meet the unique challenges they face, ensuring robust protection on any device, on any network, in any location.
– Mark Mullings, Chief Growth Officer, BlackDice Cyber
Wrapping up
As we conclude this chapter, it's important to emphasise the vast and largely untapped opportunity that the SMB market represents for telcos. With SMBs increasingly becoming targets for cyberattacks, there is a critical need for robust cybersecurity solutions tailored to their unique challenges. By focusing on this segment, telcos can not only enhance the security posture of their SMB customers; but also unlock new revenue streams, improve customer loyalty, and differentiate themselves in a competitive market.
Now is the time for telcos to invest in this high-potential market, providing the support and services that SMBs desperately need. Contact us to find out how we can help you grasp this opportunity and support your SMB customers.
-
How AI is reshaping the cybersecurity landscape
-
How AI/ML can help you build more secure, innovative products that appeal to SMB customers
A market that's ripe for disruption
Artificial intelligence (AI) has made significant strides in many fields, but its impact on cybersecurity is particularly transformative; and understanding the role of AI and machine learning (ML) in cybersecurity is essential if you're looking to grow your SMB customer base. As we saw in chapter 1, 90% of the cybersecurity market is underserved - and that's a $2 trillion opportunity for telcos to seize. It's also here where machine learning, artificial intelligence and automation present the biggest opportunity for ISPs and their SMB subscribers respectively.
Defining AI in cybersecurity
For telecom product managers, understanding the concept of artificial intelligence and how it's applied to a network as part of a cybersecurity proposition is crucial; as this forms the foundation of AI-driven cybersecurity solutions that can be offered to your SMB customers.
So let's talk "AI"...
When discussing AI in the context of cybersecurity, what we really mean is "machine learning" (ML). But what is ML?
ML is a subset of AI that trains algorithms to learn from data, recognise patterns, and make decisions with minimal human intervention. This ability to process and analyse vast amounts of data makes AI an invaluable tool in the ongoing battle against cyber threats.
On the other hand, Generative AI ("Gen AI"), is something pretty much everyone has heard of by now. It's actually a more recent development, and it works by using ML for data processing and pattern matching, creating coherent outputs based on context and instructions. You might recognise this type of AI, its capability is widely seen in tools like OpenAI’s ChatGPT and Google’s Gemini project.
Use cases for AI in cybersecurity
AI has become integral to modern cybersecurity defences and is being used to protect people, governments and organisations, in various ways:
The first use case is Automated Threat Detection.
Here, AI systems continuously analyse vast datasets to identify patterns and anomalies that might indicate threats. This is crucial as traditional methods often miss new or sophisticated exploits. For instance, AI can detect unusual activities such as unauthorised access attempts or malware distribution by learning from historical data.
For SMBs, which may lack the resources to maintain large cybersecurity teams, AI-driven automated threat detection can provide a robust first line of defence against cyber attacks.
The second use case is Proactive Security Posture.
By understanding the tactics, techniques, and procedures of past attacks, AI systems adapt to new information, allowing for proactive rather than reactive security measures. For example, if an employee’s account accesses sensitive data at odd times or from unexpected locations, AI can flag this for further investigation.
Telecom product managers can leverage this AI capability to offer proactive security features to SMB customers, ensuring their networks and data are protected before an attack can cause significant damage.
Another important use case is Network Security for ISPs.
AI helps establish a baseline of 'normal network behaviour', detecting deviations that warrant further investigation. This capability is critical in maintaining secure telecom networks, ensuring that any abnormal activity is quickly identified and addressed. For SMBs relying on telecom services, AI-driven network security can provide peace of mind, knowing that their communications and data are safeguarded against potential threats.
The dual use of AI in cybersecurity
AI in the context of cybersecurity can be viewed as something of a double-edged sword. While it enhances defence mechanisms, it’s also exploited by cybercriminals, who are constantly finding new ways to use AI to their advantage. Understanding this duality is essential for ISPs who need to anticipate and counter these threats in the solutions they develop for SMB customers.
Here are just a few of the ways that AI can be used by cybercriminals:
Cybercriminals use AI to automate reconnaissance, identify vulnerabilities, and craft sophisticated phishing campaigns. AI-generated phishing emails mimic legitimate communications, increasing their effectiveness. SMBs, often targeted due to their perceived lack of security sophistication, are particularly vulnerable to these types of attacks. ISPs must ensure that their cybersecurity offerings include robust anti-phishing tools that leverage AI to detect and block these threats.
AI is used to create adaptive malware that changes its behaviour to avoid detection by traditional security systems. This polymorphic malware can remain undetected longer, causing more damage. For SMBs, the ability to quickly identify and neutralise such threats is crucial. AI-driven anti-malware solutions can provide the necessary protection, adapting in real-time to evolving threats.
AI can analyse social media and public data to craft highly personalised attacks. It also creates realistic deepfake audio and video, which can be used in social engineering attacks to impersonate trusted individuals. As SMBs often have less sophisticated verification processes, they are particularly at risk from these types of attacks. ISPs can add value by integrating AI-driven verification and authentication processes into their offerings, helping SMBs protect themselves from social engineering and deepfake attacks.
AI systems themselves can become targets of attacks. For instance, prompt injection attacks manipulate AI model outputs, particularly those relying on natural language processing (NLP). These attacks can cause models to behave unpredictably, generating harmful or misleading responses. To counter this, explainable AI (XAI) aims to make AI models more understandable and their decisions more transparent. ISPs must consider these risks when delivering AI-powered service propositions for SMBs, ensuring that the AI models used are robust and secure against potential exploitation.
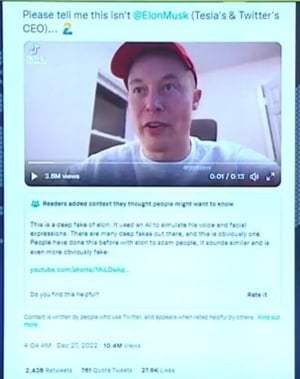
Image credit: France24/Youtube
Real world example:
Elon Musk 'deepfake'
In 2022, a deepfake Elon Musk was created by scammers and used to elicit funds via a fake investment scam, and it quickly went viral on twitter/X.
Using a digitally altered video interview of Elon Musk, an 'investment opportunity' appeared to be endorsed by Musk. In reality this wasn't the real tech billionaire but a deepfake version of him: the scammers used AI to alter a genuine interview with Musk, replacing his voice and subtly adjusting his mouth movements to match a new, fraudulent script. Believing the pitch, people were investing thousands, only to discover that the money had vanished days later, stolen by sophisticated digital scammers using advanced AI technology...
The arms race: AI versus... AI?
In cybersecurity, there is an ongoing ‘arms race’ where both attackers and defenders use AI to outsmart each other. Cybercriminals enhance their tactics with AI, while defenders use AI for automated threat detection, monitoring network traffic, and recognising malicious behaviour. This continuous cycle of attack and defence pushes the boundaries of cybersecurity technologies, driving continuous innovation. For telecom product managers, staying ahead in this arms race means continually updating and improving the AI-driven security features offered to SMB customers, ensuring they are protected against the latest threats.
The fundamentals of AI in cybersecurity
AI in cybersecurity is essential for ISPs looking to grow their SMB customer base:
-
-
-
-
Enhanced threat detection and response
AI systems will become more sophisticated in identifying and neutralising threats quickly, offering SMBs faster and more effective protection.
-
Predictive capabilities
AI will advance to predict cyber-attacks before they occur, shifting security strategies from reactive to proactive. This capability will be particularly appealing to SMBs, who often lack the resources to respond to threats in real-time.
-
Integration with emerging technologies
AI will integrate with blockchain, IoT, and quantum computing, creating more robust security systems. Telecom product managers can leverage these technologies to offer cutting-edge cybersecurity solutions to SMB customers.
-
Collaboration and information sharing
AI will facilitate real-time sharing of threat intelligence, enhancing coordinated responses to large-scale attacks. By offering SMBs access to AI-driven threat intelligence networks, telecom product managers can help them stay ahead of emerging threats.
-
-
-
Ethical considerations
The use of AI in cybersecurity can raise ethical issues; particularly around data privacy.- The collection of large datasets for AI training must balance respect for individuals’ privacy rights with regulatory compliance.
- ISPs must ensure that their solutions comply with data protection regulations, such as GDPR, while still providing effective cybersecurity.
The statistics paint a stark picture
SMBs are under constant threat from cyberattacks, yet many remain woefully unprepared. With cybercrime costs expected to exceed $10.5 trillion by 2025, the financial and operational impacts on SMBs are profound. For ISPs, these statistics underscore the urgency of offering comprehensive cybersecurity solutions. By addressing these challenges head-on, ISPs can protect their customers, build trust, and position themselves as essential partners in their customers' digital transformation journey.
Download the full guide
Download this resource as a PDF to read later, or share with your colleagues.
-
What are the stats around SMB cybercrime?
-
How many SMBs are affected globally each year?
-
How much does cybercrime cost SMBs?
Cyber crime and SMBs: understanding the risks
Let's get straight to the point: a successful cyber-attack on a small business can create utter chaos, and puts livelihoods at stake. It largely boils down to investment in cybersecurity. Small businesses often don't have the same budget to spend on defending themselves against cybercriminals. They also lack access to experts who can monitor and respond to attacks.
What does a data breach mean for a small or medium sized business?
These breaches can be very damaging to small and medium sized businesses. They don't just affect data security but also have financial consequences. By 2025, cybercrime is expected to cost SMEs over $10.5 trillion. In fact, according to Gov.uk, cybercrime costs SMBs that are breached or attacked around £15,300 ($19,650) each year; but this gets nearer to £25,700 ($33,000) when 'clean-up expenses' are included. Yes, sounds daunting but there is clean up involved: it includes restoring systems, paying ransoms, replacing hardware, and upgrading security measures post-breach.
The second major impact is harder to quantify. Business interruptions, damage to your brand reputation, and challenges in attracting future customers can all result from a single data breach. Sadly, These issues significantly increase the risk of a small business closing after an attack.
44% of consumers wouldn't spend with a business for several months after a data breach. Even more striking, 41% said they wouldn't return to the business at all. (Source: PCI Pal)
SMB cybercrime - the statistics:
Sources: [1] Proofpoint's "2020 State of the Phish Report" [2] Hiscox's "2020 Small Business & Cybersecurity Report [3] Cybersecurity Ventures' "2019 Global Information Security Survey [4] Clutch's "2020 Cybersecurity Survey" [5] Insurance Business America's "2020 Cybersecurity Survey" [6] IBM Security's "2019 Cost of Data Breach Report [7] Insurance Business America's "2020 Cybersecurity Survey" [8] Clutch's "2020 Cybersecurity Survey" [9] Cybersecurity Ventures' "2020 Global Information Security Survey"
Given these figures, it's clear why small businesses must take cybersecurity seriously to keep their doors open and protect themselves from such growing threats.
From phishing and ransomware to DDoS attacks and insider threats, SMBs face a wide array of cyber threats that can disrupt their operations and compromise sensitive data. These threats are evolving rapidly, making it crucial for ISPs to offer advanced, proactive cybersecurity solutions. By understanding the specific threats that SMBs face, ISPs can better tailor their services to meet these needs, providing their customers with the protection they need to thrive in today’s digital landscape.
In Chapter 4, we'll dive into the common cyber threats facing SMBs and then in the following chapters we'll explore how to tackle them effectively.
Ready to unlock new revenue streams in the SMB category?
BlackDice offers a comprehensive suite of cybersecurity solutions designed to protect
and manage digital ecosystems across various networks. Unlike traditional direct-to-consumer or enterprise-focused vendors, BlackDice operates on a B2B2C model. We partner with telecom operators to provide cybersecurity solutions to their end consumers and business subscribers.
and manage digital ecosystems across various networks. Unlike traditional direct-to-consumer or enterprise-focused vendors, BlackDice operates on a B2B2C model. We partner with telecom operators to provide cybersecurity solutions to their end consumers and business subscribers.
Deliver a value-added, data-driven cybersecurity service offering scalability that aligns with your growth, and the evolving needs of your SMB subscribers.
-
Overview of the common cyber threats such as phishing, ransomware and DDoS attacks
-
Examples of attacks that SMBs can face and how it impacts them
-
Emerging threats that SMBs need to be aware of

SMBs are increasingly vulnerable to a range of cyber threats.
Unlike large enterprises, SMBs often lack the robust security infrastructure and resources necessary to fend off sophisticated cyber attacks.
Cybercrime is a growing threat to all businesses, but SMBs are especially at risk. A survey by insurance firm, Markel, found that 51% of SMBs suffered a cyber attack in 2023, and this will increase by the end of 2024. The most common types of attacks are malware or viruses (24%), data breaches (16%), and phishing attacks (15%).
This chapter explores some of the most common cyber threats facing SMBs, provides real-world examples of their impact, and highlights emerging threats that every SMB should be aware of.
Phishing attacks involve cybercriminals attempting to deceive individuals into providing sensitive information such as login credentials, financial information, or personal data. These attacks often come in the form of emails, texts, or social media messages that appear to be from legitimate sources.
Impact: Phishing can lead to significant financial losses, data breaches, and damage to a company's reputation.
Ransomware is a type of malicious software designed to block access to a computer system until a sum of money is paid. It encrypts files on the affected system and demands a ransom from the victim to restore access.
Impact: Ransomware can disrupt business operations, lead to financial loss, and compromise sensitive data.
DDoS attacks aim to overwhelm a network, service, or website with a flood of internet traffic, rendering it unusable. These attacks are typically carried out using multiple compromised systems.
Impact: DDoS attacks can cause significant downtime, disrupt services, and result in lost revenue.
Impact: Insider threats can result in data loss, financial damage, and regulatory penalties.
Some examples of SMB cyber attacks and the impact it can have:
-
Example 1: Phishing attack on small retail business
A small retail business received an email that appeared to be from a trusted supplier. The email requested the verification of account details, which an employee provided.
Shortly after, the business experienced unauthorised transactions and a significant financial loss. The breach also led to customer data exposure, damaging the company’s reputation. -
Example 2: Healthcare ransomware attack
A healthcare provider fell victim to a ransomware attack that encrypted patient records and other critical data. The attackers demanded a high ransom for the decryption key. The provider faced significant operational disruption, financial loss, and legal repercussions due to the compromise of sensitive patient information.
-
Example 3: DDoS Attack on E-commerce Site
An e-commerce site experienced a DDoS attack during a major sales event, causing the site to crash and become inaccessible to customers. The downtime resulted in lost sales, frustrated customers, and a tarnished brand image.
-
Example 4: Insider threat to accountancy firm
A disgruntled employee leaked confidential client data resulting in a £30,000 fine for violating data protection regulations. Additionally, the firm lost several key clients and a 30% decrease in new client enquiries over the following months.
Emerging cyber threats that SMBs need to consider
Here are some of the most pressing cyber threats that SMBs need to be aware of and proactive against. Understanding and addressing these risks can help your SMB customers build stronger defences and safeguard their operations against potential cyber incidents.
With advancements in artificial intelligence, cybercriminals are leveraging AI to conduct more sophisticated and targeted attacks. AI can be used to automate phishing campaigns, enhance malware capabilities, and evade detection systems.
The increasing use of Internet of Things (IoT) devices in business operations introduces new security vulnerabilities. Many IoT devices lack robust security measures, making them easy targets for cyber attacks.
Cybercriminals are increasingly targeting supply chains to gain access to larger networks. By compromising a supplier, attackers can infiltrate multiple connected organisations, leading to widespread damage.
Advanced Persistent Threats (APTs) are prolonged and targeted cyberattacks where attackers infiltrate a network, remaining undetected to steal data or disrupt operations.
Wrapping up
It's clear that telcos have a significant opportunity to proactively protect SMBs from emerging threats with enterprise-grade cybersecurity. Doing so will enhance customer loyalty, reduce churn, and open new revenue streams. Now is the time to invest in AI-driven cybersecurity solutions, like those offered by BlackDice, that safeguard your customers and drive the growth of your SMB segment. For a deeper dive into these strategies and to explore AI-powered cybersecurity solutions, you can book some time in with one of our solution specialists below.
-
Understanding the difference between DNS and CPE-based cybersecurity
-
Limitations of DNS-based security
-
The case for AI-powered solutions
Traditional DNS-based cybersecurity solutions are no longer sufficient to protect SMBs from increasingly sophisticated modern cyber threats.
You may not realise it yet, but the core of your network security might be about to shift. As an ISP, it's time to embrace the power of the edge...
This chapter explores the limitations of DNS-based security and the advantages of router-based, AI-powered solutions over the limitations of traditional core DNS solutions.
Let's be honest, core DNS solutions are analogue in a digital world.
For years, the core network has relied on DNS as the gatekeeper, diligently translating domain names into IP addresses. But in a world where threats lurk beyond the URL, is DNS enough? We believe the answer is a resounding "No".

They're blind to the intricacies of data packets, oblivious to device vulnerabilities, and not much use when your subscribers step outside of their home or business network. They offer zero insights into QoE, what's causing the buffering, jitter, and frustrated subscribers. And with the rise of DNS over HTTPS (DoH) – core DNS is simply lost in the dark.
– Paul Jenkins, Co-Founder and CISO, BlackDice Cyber
Soundbite:
Transition from DNS to router-based cybersecurity
From DNS to router-based cybersecurity, how can telcos overcome the challenges?
Here, CEO Paul Hague says it's "pretty straightforward" with BlackDice's solution:
"The idea is to be the interface between the DNS decisions and the DNS resolution"...
So where do we go from here?
The future lies not in the corners of the core network, but at the edge, with AI-powered software running on routers. Imagine this: a security solution that lives at the network's edge, embedded within your router hardware. This AI-powered software, and it's already here, pioneered by BlackDice Cyber. It boasts some significant benefits over traditional core DNS solutions, as outlined in the figure below.
Benefits of router-based cybersecurity vs core DNS:
Deep network visibility
It sees everything, from device types and vulnerabilities to traffic patterns and anomalies. No more blind spots.
Proactive threat detection
AI analyses this wealth of data in real-time, identifying and stopping threats before they can wreak havoc.
Unparalleled QoE insights
Forget guesswork. This software pinpoints the root cause of buffering and latency, ensuring a seamless user experience.
DoH-proof security
It doesn't shy away from encrypted DNS requests, offering comprehensive protection regardless of protocol.
By deploying AI-powered software on your routers, ISPs can unlock a significant number of new opportunities and benefits across your operational, product innovation and commercial functions:
Reduced churn and happier subscribers
Proactive protection and improved QoE mean satisfied customers who stick around.
Enhanced brand reputation
Be known as the provider that takes security seriously, attracting more SMBs.
Creates significant
cost savings
cost savings
Early threat detection translates to fewer breaches and lower remediation costs.
Future-proof your network infrastructure
This technology adapts and evolves, keeping you ahead of the evolving threat landscape.

This isn't just about technology; it's about empowering your people and your business to deliver better services and experiences to your customers. Equip your teams with the insights and tools that AI-driven cyber data provides, and watch them transform from reactive to proactive, maximising every opportunity for revenue growth and a better quality of experience.
– Sarah Hague, COO, BlackDice Cyber
Wrapping up
With the rich data collected by routers to fuel your AI engine, you'll get invaluable insights for threat detection, QoE optimisation, and a future-proof security posture. As networks evolve, edge-based security will become increasingly crucial. Be an early adopter and reap the benefits of a proactive, data-driven approach.
Traditional DNS-based security methods, while useful, are no longer sufficient in today’s threat landscape. Router-based security, enhanced by AI and machine learning, offers a more comprehensive and future-proof solution. For ISPs, transitioning to router-based security means providing a higher level of protection for their SMB customers, reducing the likelihood of successful cyberattacks, and improving overall network resilience. This shift not only enhances security but also drives customer satisfaction and loyalty.
Ready to see BlackDice AI technology in action?
-
Understanding market segmentation
-
Understanding customer needs
-
Building your SMB value proposition
Segmenting the market: what you should know
Understanding your market is the first step in creating a successful product marketing strategy. SMBs are a diverse group, and a one-size-fits-all approach won’t work. Effective segmentation allows you to tailor your marketing efforts to different sub-segments within the SMB market. Here a three ways you can segment your existing (and new) SMB customers:
-
First, look at the Industry (also known as 'Vertical' or 'Sector'): Segmenting SMBs by industry can help tailor your offerings to meet specific needs. For example, healthcare SMBs may prioritise data security due to compliance requirements, while retail SMBs might focus more on protection against point-of-sale malware.
-
Second, consider the business size and maturity: SMBs vary greatly in size and sophistication. Smaller, newer businesses may require more basic solutions and education, while larger, more established SMBs might be looking for advanced features and scalability.
-
Third, look at geographic locations / territories: Consider the regional differences in cybersecurity awareness, regulation, and threat landscapes. Tailor your messaging and offerings to address these regional nuances.
Have you got the right product-market fit?
Defining product-market fit
Achieving product-market fit is the cornerstone of any successful product launch, especially in the competitive world of cybersecurity solutions for SMBs. For telecom operators, understanding and achieving product-market fit means ensuring that their cybersecurity offerings not only meet the needs of SMBs but also do so in a way that is scalable, profitable, and sustainable.
Product-market fit occurs when a product satisfies a market demand.
For telcos, this means offering cybersecurity solutions that:
- Address real pain points: Your solutions must solve actual problems faced by SMBs, such as protecting against cyber threats, ensuring regulatory compliance, or safeguarding customer data.
- Provide value: The benefits of your solution must be clear and measurable, whether through cost savings, enhanced security, or improved operational efficiency.
- Are scalable and sustainable: this means solutions that grow with the business, offering scalability without compromising on quality or performance.
So what are the steps to achieve it and the indicators that signal its attainment?
These are the three core areas you need to focus on when looking to create product-market fit:
Before launching a new cybersecurity product, extensive market research is essential. This involves:
Identifying your target audience: Clearly define the SMB segments you are targeting. Are they in specific industries, regions, or of a particular size?
Understanding customer needs: Engage directly with SMBs to understand their cybersecurity challenges, needs, and expectations.
Competitor analysis: Assess what your competitors are offering and identify gaps in the market that your product can fill.
Achieving product-market fit often requires an iterative approach to product development:
MVP (Minimum Viable Product): Start with a basic version of your product that addresses core needs. Use this to gather feedback from early adopters.
Feedback loop: Continuously collect feedback from SMBs using your product. Understand what works, what doesn’t, and where there are opportunities for improvement.
Rapid iteration: Quickly implement changes based on feedback, refining your product to better meet market demands.
Testing your product in real-world conditions is crucial:
Pilot programmes: Run pilot programmes with selected SMBs to test your product in a controlled environment. This allows you to identify any issues before a full-scale launch.
Performance metrics: Track key performance indicators (KPIs) such as adoption rates, customer satisfaction, and retention rates to gauge how well your product is performing.
Market response: Monitor how the market responds to your product. Are SMBs willing to pay for it? Are they recommending it to others?
Focus on these four indicators of product-market fit:
SMBs continue to use your product over time and express satisfaction with its performance. They renew their subscriptions, upgrade to higher service tiers, or purchase additional features, indicating that your product is meeting their needs effectively.
When customers start recommending your product to other SMBs, either within their industry or through online reviews and testimonials, it’s a strong sign that your product resonates well with the market.
If you’re consistently seeing an increase in demand for your product, whether through new customer sign-ups, inquiries, or organic website traffic, it’s a good indication that your product-market fit is solid. This could also be reflected in the reduction of churn rates and an increase in the average revenue per user (ARPU).
If your product starts to be recognised as a leading solution within its category, either through industry awards, media coverage, or customer feedback, it suggests that you’ve established a strong product-market fit. This can also manifest in competitors trying to emulate your features or pricing models.
Positioning your new cybersecurity product/service in your target market
Once you have a product that meets market needs, focus on how to position it effectively. You'll need a simple, clear value proposition that really articulates the unique value your product offers. For example, how does it solve SMB challenges better than existing solutions? Then you'll need to look at your messaging: how will you communicate with your audiences? Tailor your messaging to resonate with different SMB segments and use simple language that speaks directly to their specific needs and concerns.
Finally, you'll need to consider your channel strategy when positioning your product/service. What are the best channels to reach your target audience, whether through direct sales, partnerships, or digital marketing?
Building your SMB value proposition
Understanding your customer needs
As an ISP product manager, you'll know that to develop a value proposition that truly resonates with SMBs, it's essential to first understand their specific pain points and requirements. As we've already explored in chapters 3 and 4, SMBs typically have limited resources, both in terms of budget and expertise. They require solutions that are not only cost-effective but also easy to implement and manage.
So what is the market need and how can you develop propositions to meet this demand?
Based on what we've covered in previous chapters, SMB customer needs can generally be broken down into four categories: Security, Scalability, Sensitivity and Simplicity. Learn more by expanding the boxes below:
Given these needs, telcos can differentiate themselves by offering tailored solutions that directly address these challenges.
Here are some ideas:
One effective way to add value for SMBs is to bundle cybersecurity solutions with your existing connectivity offerings. For example, offering a router-based AI-powered security solution alongside internet service can provide SMBs with comprehensive protection against cyber threats.
Provide different service tiers to cater to various budgets. A basic tier might include essential cybersecurity features, while a premium tier could offer advanced analytics, threat detection, and data insights.
Given that SMBs often lack in-house IT expertise, providing dedicated customer support that understands the unique needs of small businesses can be a key differentiator.
SMBs appreciate the ability to customise their services to fit their specific needs. Offering flexible plans that allow them to scale services as they grow can be highly appealing.
Create messaging that resonates
Effective messaging is critical to conveying the value of your offerings to SMBs. When it comes to communicating your SMB value proposition, make sure you remember to simplify the complex. Cybersecurity can be a confusing topic, especially for non-experts. Your messaging should break down these complexities into easily understandable benefits.
Top tip: Focus on how your solutions make the SMB’s life easier (solving those pain points), rather than on the technical details.
For a lot of small businesses, a cyber attack can significantly impact people's livelihoods. That's why when communicating your messages, emphasise how your offering gives them peace of mind. Highlight how your solutions protect their business, reduce risk, and provide reassurance, allowing them to focus on their business and growth.
There's nothing more resonant than real-world data and case studies to demonstrate the effectiveness of your solutions. For instance, showing how your cybersecurity offering has reduced incidents for similar businesses can build trust. Include testimonials and case studies from satisfied customers to build credibility and demonstrate the tangible benefits of your offerings.
Scaling and growth
After achieving product-market fit and a clear positioning, scaling your product and expanding your market presence become the next critical steps. Here, we'll explore how to effectively manage this phase.
Once you’ve established a strong foothold in one market segment, consider expanding into new geographic regions or industry verticals where similar needs exist. For example, if your cybersecurity product has been successful among SMBs in the healthcare sector, explore opportunities in other highly regulated industries like finance or retail, where security and compliance are also top priorities.
Continuously enhancing your product to meet evolving customer needs is crucial. This could involve developing additional features, such as advanced threat detection, AI-driven analytics, or enhanced data protection tools, that complement your core offering. Extensions could also include introducing new service tiers, such as premium packages that offer more comprehensive coverage or faster response times.
Form strategic partnerships with technology providers, Managed Service Providers (MSPs), or industry associations to broaden your product’s reach and add value for your customers. For instance, partnering with cloud service providers could enable you to offer integrated solutions that combine cybersecurity with cloud storage and management, appealing to SMBs looking for comprehensive digital protection.

There's nothing more resonant than real-world data and case studies to demonstrate the effectiveness of your solutions. For instance, showing how your cybersecurity offering has reduced incidents for similar businesses can build trust. Include testimonials from satisfied customers to build credibility and demonstrate the benefits of your offerings.
– Mark Mullings, Chief Growth Officer, BlackDice Cyber
Wrapping up
Achieving product-market fit is crucial for the success of any cybersecurity offering. By thoroughly understanding the needs and pain points of SMB customers, ISPs can develop solutions that resonate with their target market. This alignment not only ensures the effectiveness of the product but also drives adoption and long-term success. For ISPs, focusing on product-market fit means delivering solutions that meet the evolving needs of SMBs, ultimately leading to increased customer retention and growth.
Ready to learn more about AI-powered cybersecurity and data intelligence?
Cyber data: the untapped opportunity for ISPs
For telecom operators, the vast amounts of data generated through network interactions present a significant opportunity, not just for enhancing service delivery, but also for creating and enhancing revenue streams. By leveraging advanced cybersecurity solutions, particularly those powered by AI and machine learning, telcos can transform raw data into actionable insights, offering value-added services to their SMB customers.
This chapter explores the strategies and potential of monetising cyber data, emphasising how this approach can drive new revenue streams while improving customer loyalty, QoE and satisfaction.
Understanding cyber data
Cyber data encompasses all of the information that's generated from monitoring, detecting, and analysing network traffic, user behaviours, and potential threats. For telcos, this data can include:
Understanding how data flows through the network, identifying peak usage times, and recognising abnormal traffic that might indicate a security threat.
Data on emerging threats, attack vectors, and potential vulnerabilities specific to the SMB sector.
Insights into how SMBs and their employees interact with digital services, including the types of devices they use, their browsing habits, and their engagement with different online platforms.
Information about the various devices connected to the network, including their security postures, vulnerabilities, and potential risks.
Hear from our CEO, Paul Hague, discussing the benefits of cyber data to ISPs.
Here we dive into how our AI algorithms identify devices on your network, make crucial data connections, and open up new marketing opportunities for product/service upsell and cross sell.
In this soundbite, catch our team discussing how our data intelligence technology helps operators better understand and serve their subscribers.
Transforming data into insights
The true value of cyber data lies in its transformation into actionable insights. This process involves several key steps:
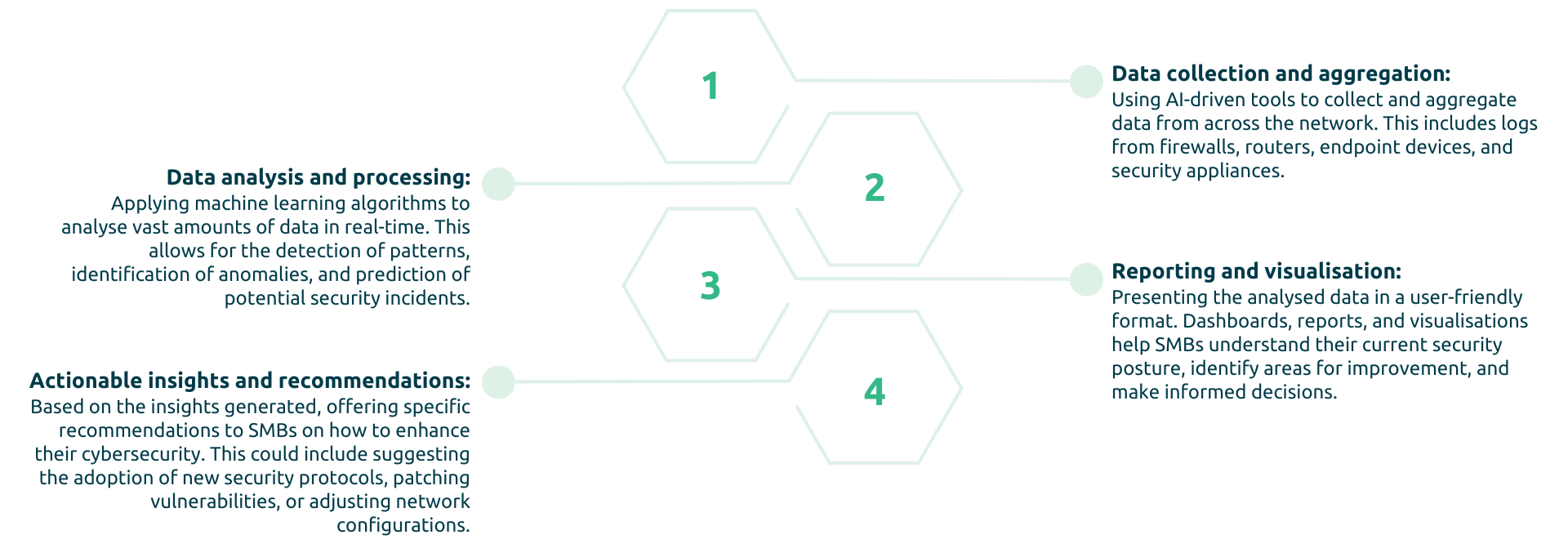
Monetising cyber data
Monetising cyber data presents a significant opportunity for ISPs to enhance their service offerings, drive new revenue streams, and build stronger relationships with SMB customers. With advanced analytics, AI, and machine learning, operators can transform raw data into valuable insights that help SMBs protect their networks, meet regulatory requirements, and make informed business decisions.
However, success in this area requires a careful balance of technical capability, regulatory compliance, and customer education. With the right strategy, you'll position your ISP as leaders in the SMB market, offering solutions that go beyond basic protection to deliver true business value.
What can ISPs do with all their network data and insights?
Once cyber data has been transformed into valuable insights, telecom operators can monetise this information in several ways. Here are a few ideas below:
Offer data-driven cybersecurity services as a premium add-on to existing connectivity packages. SMBs can subscribe to services that provide continuous threat monitoring, real-time alerts, and personalised security recommendations.
Create different service tiers based on the depth and breadth of insights provided. Basic tiers might include standard threat detection, while premium tiers offer advanced analytics, detailed reporting, and 24/7 support.
Position data analytics as a standalone service. SMBs could subscribe to access detailed analytics on their network security, user behaviour, and potential vulnerabilities, allowing them to make data-driven decisions.
Help SMBs meet regulatory requirements by providing data that demonstrates compliance with cybersecurity standards. This could be particularly valuable in sectors like healthcare, finance, and retail, where data protection regulations are stringent.
Offer SMBs the ability to customise their reports based on their specific needs. For example, a healthcare SMB might require detailed insights into patient data protection, while a retail business might focus on securing payment transactions.
There are numerous benefits to telecoms operators, by monetising the cyber data on their networks. It not only generates new revenue streams but also strengthens the relationship between your brand and your SMB customers:
By offering premium cybersecurity services, operators can increase the average revenue generated from each SMB customer.
Providing valuable insights and personalised recommendations helps build trust and loyalty among SMBs. They are more likely to stay with a provider that offers them added value beyond basic connectivity.
Offering advanced, data-driven cybersecurity services can differentiate telecom operators in a crowded market. This is particularly important as SMBs become more discerning in their choice of providers.
When SMBs see the tangible benefits of enhanced cybersecurity and data analytics, they are less likely to switch providers. This reduces churn rates and contributes to long-term revenue stability.

With advanced analytics, AI, and machine learning, operators can transform raw data into valuable insights that help SMBs protect their networks, meet regulatory requirements, and make informed business decisions.
– Mark O’Neill, Chief Technology Officer, BlackDice Cyber
Wrapping up
Cyber data is a valuable asset that, when leveraged correctly, can drive significant revenue growth for ISPs. By analysing network data, ISPs can gain insights into customer behaviour, identify potential threats, and offer tailored solutions that meet the specific needs of their SMB customers. This not only enhances security but also creates opportunities for upselling and cross-selling additional services.
Monetising cyber data isn't just about generating revenue; it’s about using data-driven insights to deliver better, more personalised experiences for customers, ultimately driving long-term loyalty and growth.
-
How a European ISP is delivering cybersecurity to its SMB customers with BlackDice
-
Challenge: How to distinguish their offerings to reach new markets?
-
Solution: A white label solution integrated into their hardware
Challenge
A premier private internet service provider in Europe came to BlackDice with a challenge: how to distinguish their offerings to reach new markets and attract more SMB subscribers? With an aim to achieve substantial customer-base coverage in six months from deployment, they needed effective market differentiation to better serve both current and new SMB customers.
Solution
-
Deep network visibility:
Developed a ready-to-deploy product focused on total device protection with real-time defence against digital threats. -
Go-to-market strategy:
Collaborated on the product’s Go-To-Market strategy and rollout plan targeting both new and existing customers.
-
Unparalleled QoE insights:
Integrated a white-label solution into existing router hardware. -
Intuitive mobile app:
For SMB end users, an intuitive mobile app to empower them with complete network visibility and control, with features like device management and instant internet pause functionality.
Machine learning analyses vast amounts of data in real-time. This allows for the detection of patterns and anomalies that might indicate potential threats. Unlike traditional methods that react to known threats based on predefined signatures, AI can predict and prevent new, unknown threats before they cause harm. This shift from reactive to proactive security is a game-changer for ISPs offering real-time threat neutralisation, with no down time
WiFi scheduling promotes balanced screen time, while SMBs benefit from robust data breach protection and network optimisation
CEO of the European ISP, commented on the solution:
With BlackDice’s AI successfully integrated into our network infrastructure, it’s proving to be extremely effective for delivering enterprise-grade threat prevention and management to our SMB subscribers. We can now better serve SMBs by ensuring continuous connectivity, giving visibility of all devices on the network – at home, in the office, or travelling for business”
Download this case study
Download this case study as a PDF to read later, or share with your colleagues.
-1.png?width=400&height=400&name=home-hero-image%20(1)-1.png)
Where do you go from here?
As we wrap up this guide, it's clear that the SMB market presents a significant growth opportunity for telecom operators. The increasing cyber threats faced by SMBs are driving the need for robust, scalable cybersecurity solutions.
“By helping SMBs address the threats they face, telcos can not only protect their customers but also enhance their own offerings, reduce costs to serve, and ultimately increase ARPU and QoE significantly.”
Your next steps should include:
Assess your existing value propositions and identify areas where you can introduce or enhance cybersecurity services.
Begin integrating AI-powered tools to gain deeper insights into network behaviour and to enhance your cybersecurity measures.
Consider partnering with technology providers like BlackDice, who can offer advanced, tailored cybersecurity solutions for your SMB customers.
Ensure that your teams and your SMB customers are fully informed about the evolving cyber threats and the solutions available to combat them.
By taking these steps, you’ll be well on your way to not only safeguarding your customers but also driving growth and innovation within your own business.
The SMB market is greatly underserved, and with the right approach, you can be at the forefront of this transformation, delivering real value to your customers and achieving your business goals.
Future outlook
AI is set to play a central role in the future of cybersecurity in the telecoms sector. It will help telco product managers in developing solutions that meet the needs of their SMB customers. While there are challenges, the continuous evolution and improvement of AI technologies promise a more secure digital landscape.
We believe the future is promising; one where security and intelligence go hand in hand, and those operators who embrace this vision will be the ones leading the charge, owning their category and increasing their market share.
These technologies empower operators to offer advanced cybersecurity services that are proactive rather than reactive, protecting SMBs while also generating valuable insights that can be used to optimise network performance and improve overall customer experience.
The path forward involves more than just implementing basic security measures, it requires a strategic approach that leverages AI, machine learning, and deep data intelligence.
Hi, we're BlackDice.
We exist to build confidence in the connected world by pioneering a safer digital future, for everyone.
We exist to build confidence in the connected world by pioneering a safer digital future, for everyone.
This helps operators to:
Our AI-powered cybersecurity allows operators to spot patterns and anomalies on their networks. This helps keep people and businesses even safer, as operators will have the technology to counter threats and fix problems faster, or before they even happen.
Data intelligence helps operators understand why their subscribers call, when they call and what they could do to prevent it. As well as making call centres more efficient and reducing costs, BlackDice also helps operators attract and retain subscribers by providing insights to help them improve the quality of experience they provide.
By 2030, society will
be using over 50 billion vulnerable devices.
be using over 50 billion vulnerable devices.
But we're out to change that. To make sure that those devices are safe, and people can have confidence while connected. We believe everyone has the right to work, learn and play online, with the confidence that they’re protected.
On any device, on any network, in any location.
How we do it
We help network operators keep people and businesses safer online – and serve their subscribers even better, through our Technology, Data, Knowledge, and People.
Technology
Today, we work with network operators and hardware manufacturers around the globe, adding our AI-powered cybersecurity technology to routers to protect families and businesses. BlackDice technology protects anything with an IP address, and in the future, we’ll look to scale into other industries, keeping people and devices safe while they’re connected.
%20(5)-1.png?width=280&name=BlackDice%20smb%20guide%20mock%20up%20(Instagram%20Post)%20(5)-1.png)
.png?width=280&height=280&name=factsheet%20(1).png)
.png?width=200&height=50&name=Blackdice%20logo%20white%20(1).png)